In the era of cybertechnology, more applications are being adopted and more information is getting to the public. This poses security risks as not all information is meant to be publicized. When landed in the wrong hands, it may result in data breaches and revenue loss — worst, ruined business.
With your digitalization journey, it is important to assess the applications and technologies that you will implement in your business. Apart from its functionalities, you also need to prioritize the security features to prevent cyber and data risks.
If you are looking for a secure meeting management platform in Teams, Convene in Teams is a great option as you get both its smart functions and state-of-the-art security features. In this article, you can learn more about AES 256-Bit Encryption and why it’s one of the best security features in the market.
What is Encryption?
Encryption is a security method of encoding information by converting plaintext (unencrypted data) into ciphertext (encrypted data). The ciphertext is the ‘secret code’ to hide the true meaning of the information. To encrypt and decrypt information, one should be knowledgeable about cryptography.

Effective encryption makes use of a variable or key as part of the formulas or algorithms. When an unauthorized person tries to intercept an encrypted message, the intruder would need to know which cipher and keys have been used to encrypt the message. What makes it an effective security method is the time and difficulty it poses for the intruder to guess.
Such a security tool is essential in providing confidentiality and integrity to the content it protects, as well as the authentication of verified individuals who access the content. Furthermore, it supports nonrepudiation to prevent individuals from denying they sent the encrypted message.
What is AES Encryption and how does it work?
Encryption has cultivated a culture of security and privacy in today’s digital world. First that has been standardized is the Data Encryption Standard algorithm (DES). However, because of its slow processing and easy cracking, it was replaced by a more robust algorithm, the AES.
AES stands for Advanced Encryption Standard which is a symmetric block cipher formula with 128 bits as the block size. This means that only the sender and receiver have the key to decrypt and render the ciphertext unreadable to intruders. It allows conversion of the individual blocks using keys of 128, 192, and 256 bits. Once the blocks are encrypted, the algorithm connects them together to form the ciphertext. AES is based on a substitution-permutation network (SP network) that includes replacing inputs with specific outputs and shuffling.
Each key length has a different number of possible key combinations and varies in three lengths:
- 128-bit key length: 3.4 x 1038
- 192-bit key length: 6.2 x 1057
- 256-bit key length: 1.1 x 1077
Understanding how AES encryption works is quite simple. A single block is composed of 16 bytes, which is a 4×4 matrix. Each byte has 8 bits in it, adding up to create a block of 128-bits. Then, the AES algorithm is applied to each block. The key being used initially is expanded into (n+1) keys, n being the number of rounds in the encryption process.
The algorithm runs through these six steps:
- Key Expansion — Round keys are created to be used in the next stages of encryption. This stage follows Rijndael’s key schedule.
- Round Key Addition — The round key is the result of performing an operation on the previous round key and the data to encrypt. The initial round key is added to the divided data.
- Byte Substitution — Using the Rijndael S-box substitution, the AES algorithm substitutes each byte with a code. At this stage, the elements in a row of a block may look like this: 8d 08 05 5s
- Row Shifting — The rows of a block from the byte substitution process move to the left. The first row remains, but the second row gets shifted to the left by one byte, the third row by two bytes, and the last row by three bytes.
- Column Mixing — With a predefined matrix, each column is multiplied, creating a new block of code. This step involves a lot of advanced mathematics.
- Round Key Addition — In this step, the round key from the key expansion step is applied to the columns.
This process is repeated for many more rounds, specifically 9 times for the 128-bit key, 11 times for the 192-bit key, and 13 times for the 256-bit key.
How secure is 256-bit AES Encryption?
The “bit” refers to the length of key required to cipher and decipher the encryption. AES 128-bit encryption alone has been proven to be a robust security tool as it would take billions of years even for a supercomputer to decipher the code. The 256-bit AES Encryption then is on another level.
As there is no “best encryption method” in the market as different organizations may require different types of codes, AES is one of the most secure single-block encryptions in today’s age. So long as the encryption is properly implemented, your confidential content is protected.
With such a standard for encryption, AES has been trusted by various government agencies and companies worldwide to encrypt their digital assets.
Why Convene in Teams Uses AES 256-bit Encryption
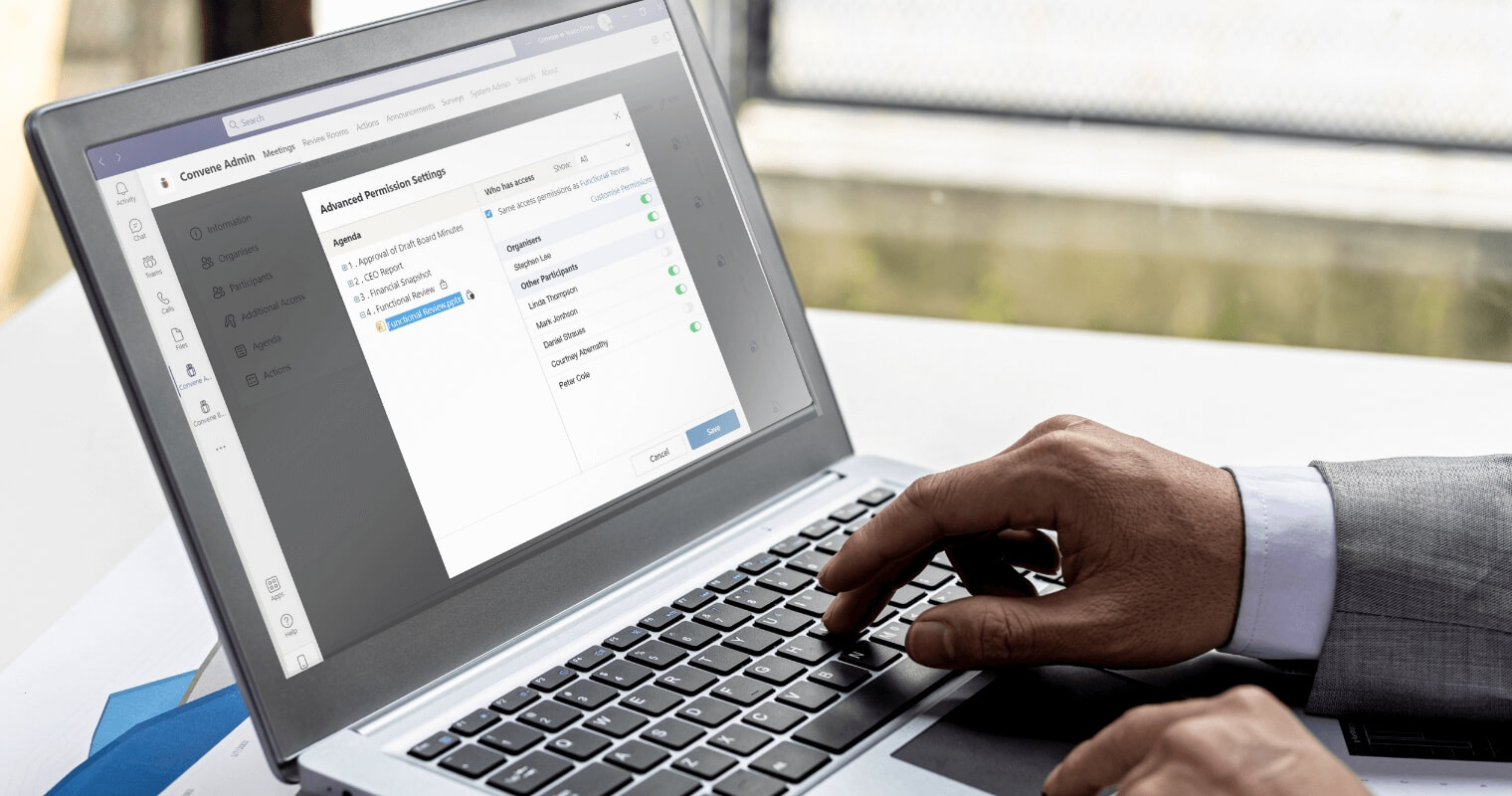
Convene in Teams (CiT) is a meeting management platform in Teams designed to empower collaboration, productivity, and governance in structured meetings in the Microsoft space. Developed with the same industry security standards as Convene, CiT comes with advanced security features and controls, including AES 256-bit encryption.
CiT’s number one priority is the satisfaction of our customers and clients, which is why we keep in mind that in every stage of your meeting process, we protect your digital assets. We are here to keep your meetings and data smart, simple, and secure. Governments and companies across the globe have trusted our services, as we are also a CMMI-Level 5 company with over three decades of experience in developing secure software.
Our security measures go beyond encryption — CiT has adopted all of the notable security features of Convene, including:
- Granular access controls and role-based permissions
- Document security and digital rights management
- Device security
- Multi-factor user authentication
- Security governance
- System administrator control
- Enterprise-grade cloud infrastructure
- Usage reporting and audits
Learn more about what else Convene in Teams can do to run better meetings in Teams apart from high-grade security. Talk to our team now!
Audrey is a Content Marketing Specialist at Convene, in charge of managing the production of quality content on the company’s website. A communication major keen on marketing, Audrey has been constantly seeking approaches to create tailored content—may it be about governance, digitalization, boards, or meetings—fit for the stakeholders. When not strategizing on the next ebook to produce, Audrey finds solitude in reading make-you-ugly-cry novels and listening to self-improvement podcasts.









